| Home | Videos | Slides | Assignments & Resources | Tests | Exams | YODA Topics | Hall of Fame |

An EEE4084F Hall of Fame winning project |
 |
The DEATHSTAR:
Data Encryption Accelerator That Handles Security Tasks Anytime Readily

By Lynn Asiimwe, Victor Mushabe, Daniel Galasko (Project P15, 2012)
Problem and Proposed Solution
In today’s world the security of sending information over a network is a top priority. One means of combating the interception of data over a network is by using a process called encryption.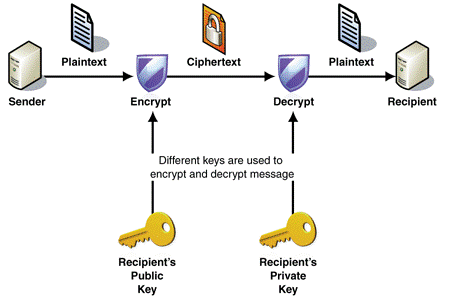
Figure 1. A brief overview of encryption
As computers use encryption more and more the bottleneck of the speed of the encryption process performed by the CPU becomes increasingly evident. The solution is to design a Data Encryption Accelerator (DEA) that can perform data encryption for a computer instead of relying on the CPU thus improving the speed of the encryption process and removing added strain on the CPU by performing encryption calculations.We propose the DEATHSTAR (Data Encryption Accelerator That Handles Security Tasks Anytime Readily) whose primary objective is to accelerate the process of encrypting a data stream.
Problem list/design questions to be solved
The obvious solution to accelerating encryption is through parallelization. By dividing a message into chunks and encrypting each chunk in parallel a significant speedup can be performed. This can only occur if different parts of the message can be operated upon independently. The only problem with this is that the size of the message needs to be known and so the system would need to wait for all the data to be available.It must also be noted that certain messages might be too small to notice any speed up in parallel.
CTR mode is a particular encryption mode that is easily parallelizable. In CTR mode the keystream is computed in blocks where each block is generated by encrypting a unique plaintext block, this allows the blocks to be processed in any order. Other encryption schemes rely on the ciphertext for a previous block in order to create the ciphertext for the current block thus making parallelization significantly more difficult.
Another means of achieving speedup is through interleaving. In interleaving the message is separated into two different plaintexts and has each processor handling different blocks.
Identify Suitable Criteria for an Acceptable Solution
The encryption process needs to be such that it does not add a significant overhead to the time taken to send the message. The DEATHSTAR must therefore ensure that encryption time is hardly noticed and that the main delay is due to network bandwidth or speed etc. It would also be desireable to ensure that the DEATHSTAR can achieve encryption at a rate significantly higher than a system performing the same encyption in serial.References:
www.spamlaws.com/data-encryption.htmlwww.ecu.edu/cs-itcs/itsecurity/DataEncryption.cfm
i.msdn.microsoft.com/dynimg/IC155063.gif
etutorials.org/Programming/secure+programming/Chapter+5.+Symmetric+Encryption/5.13+Parallelizing+Encryption+and+Decryption+in+Modes+That+Allow+It+Without+Breaking+Compatibility/
 |
Download the project (.zip) |
